Multi-Factor Authentication (MFA)¶
Overview¶
To enhance the security of the Mber+ admin portal, Multi-Factor Authentication (MFA) is now enabled for all admin users. This feature requires admin users to verify their identity using a one-time passcode generated by an authenticator app, in addition to their standard login credentials.
MFA setup is mandatory for admin users and uses a Time-based One-Time Password (TOTP) mechanism via Google Authenticator or Microsoft Authenticator.
Prerequisites¶
- You must have Google Authenticator or Microsoft Authenticator installed on your mobile device.
- You must complete the MFA setup before accessing the admin portal if it has not been configured previously.
Setup Steps (First-Time Users)¶
- Login with your username and password as usual.
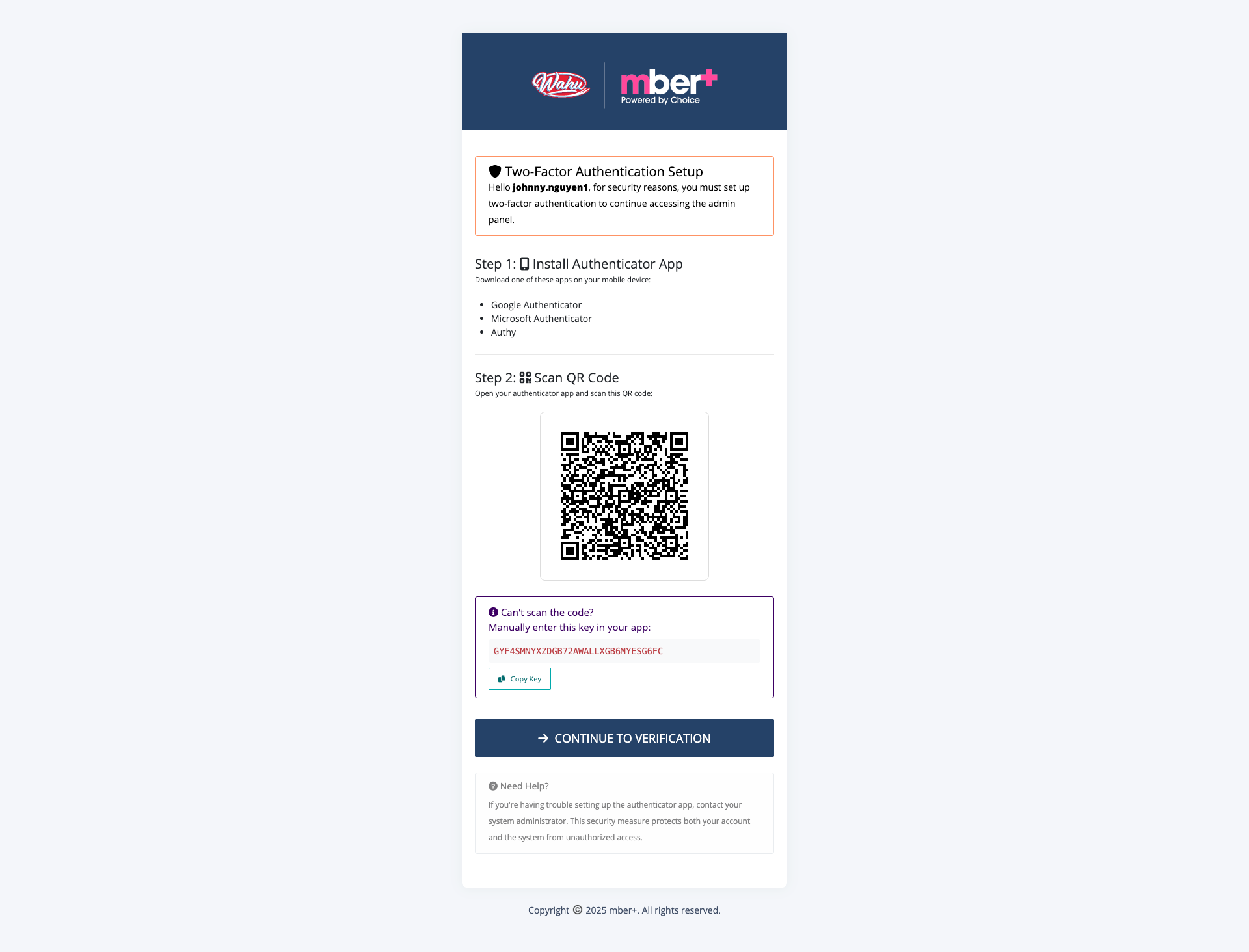
- You will be redirected to the MFA Setup screen.
- Open your preferred Authenticator app (Google or Microsoft).
- Scan the QR code displayed on the setup screen or enter the manual key provided.
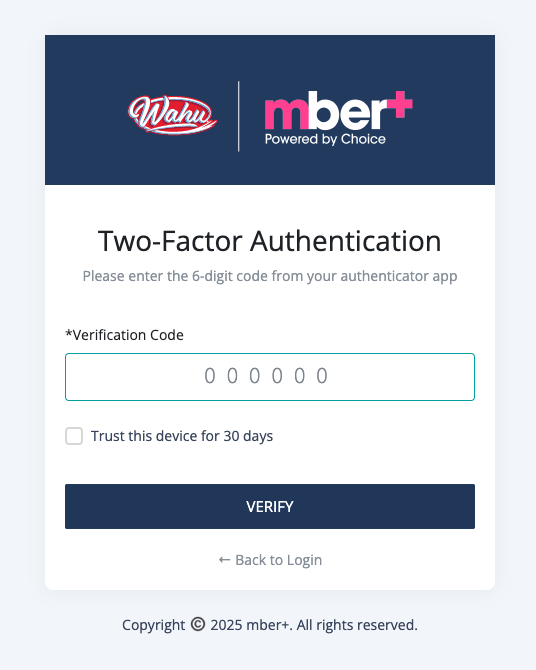
- Enter the 6-digit code generated by the app to verify your setup.
- Optionally check “Remember this device for 30 days” if you do not want to be prompted again from the current device.
- Upon successful verification, MFA will be enabled and required for future logins.
Note: If you do not complete the setup, you will not be able to access the admin portal.
Remember This Device (30 Days)¶
- You can opt to trust your current device for 30 days.
- If enabled, you won’t be prompted for MFA on this device for 30 days.
- After 30 days, you will be prompted again.
- Trusted devices can be revoked by other administrators.
Resetting MFA¶
- Admin users can reset MFA setup.
-
When MFA is reset:
-
The admin user will be required to set up MFA again on next login.
- All trusted devices will be cleared.
- The
TwoFactorEnabledflag remains true, but setup is marked as incomplete.
Backend Setup¶
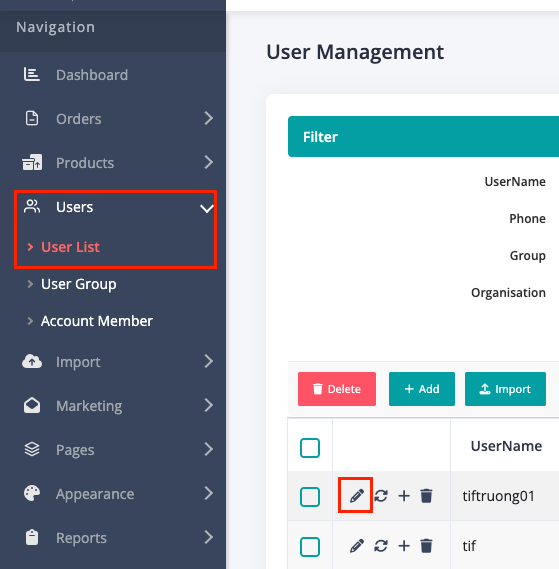
- MFA setups can be found under menu Users -> User List -> Add / Edit User.
Role-Based Control¶
| Role | Permission |
|---|---|
| Super Admin | Can enable/disable MFA for other admins |
| Admin (TPF / Client) | Must complete setup if MFA is enabled for them |
| Admin (TPF / Client) | Can reset MFA setups |
Troubleshooting¶
- Authenticator app not generating code? Ensure your phone’s time is set automatically.
- Lost your device? Contact your Super Admin to request an MFA reset.
- Changed your phone? You will need to reset MFA and scan the new QR code.
Security Notes¶
- Authenticator keys are securely stored and never shared.
- Trusted devices are device-specific and expire automatically after 30 days.
- MFA setup and verification logs may be audited for compliance.
FAQs¶
Q: Can I disable MFA for my account?
A: No. MFA is enforced for all admin users by system policy.
Q: What if I delete my authenticator app?
A: Request an MFA reset from a TPF Admin or Client Admin users.
Q: How do I know if my device is trusted?
A: Trusted devices do not prompt for MFA. You can revoke them in the User's settings if available.